
Hi there! Did you know that...
 3,000,000
3,000,000
About three million people had their computers affected by a spyware application within the last 12 months.
 10,000,000
10,000,000
Over ten million new malware applications are created, and then released in the wild each month.
 1,000,000,000
1,000,000,000
It is estimated that the total number of malicious programs has exceeded one billion this year.
Welcome to Eradicate Spyware!
My name is Josh. I am an IT security consultant. I help businesses of all sizes keep their computers & networks secure and/or get rid of any type of malware, including complex spyware and ransomware.
Does your company work with a security researcher?
DISCOVER WHAT I DO FOR A LIVING
RECENT SECURITY NEWS
 Dell announces cybersecurity incident
Dell announces cybersecurity incident
Dell has recently disclosed that an unknown group of hackers has managed to infiltrate its network. On November 9, 2018, the company detected and disrupted unauthorized activity on its servers. The attackers attempted to extract customer information, which was limited to names, email addresses and hashed passwords. Dell has decided to reset their customers’ passwords, with the goal of protecting all the accounts.
 Pwn2Own 2018 hackers receive $267,000
Pwn2Own 2018 hackers receive $267,000
The popular hacking competition has brought white hat hackers a total of only $267,000 out of the $2 million prize. Surprisingly, Microsoft Edge, Apple's Safari, Oracle's VirtualBox and Mozilla Firefox appear to be much stronger in comparison with last year's versions, when cybersecurity experts managed to earn an impressive $833,000 from Zero Day Initiative. Richard Zhu won the Master of Pwn award this year, receiving a total of $120,000.
 New Meltdown and Spectre vulnerabilities
New Meltdown and Spectre vulnerabilities
Researchers from Graz University of Technology, imec-DistriNet, KU Leuven and College of William and Mary, along with some of the experts who devised the original Meltdown and Spectre attacks, have disclosed seven new variants that leverage transient execution. According to them, exception or branch misprediction events may leave secret-dependent traces in the CPU's microarchitectural state.
RECENT SECURITY GUIDES

Strong password tips and enterprise-level alternatives
Choosing a strong password is essential for business owners. If your passwords are weak, company data may be exposed, your business may lose a lot of money, and most of all its clients' trust. Sadly, many people continue to use weak passwords such as "123456", "qwerty", "password", and so on. Believe it or not, these examples come from ABC's top 100 passwords list, and they have easily made it into top 10. Here's the link to the article, in case that you are interested in finding out what passwords need to be avoided at all costs.
So, how do you choose a strong password, which will guarantee that your data stays within the company premises? The obvious step is to pick a password that is hard to guess. Don't use common words, even if you add some randomness to them by including some numbers, for example. So, avoid using passwords such as "Facebook1980", to give you an idea. That password may look okay, but it will get cracked within minutes by any brute-force attacker which makes use of a dictionary.
These days more and more companies utilize password managers. While I don't dislike them, I wouldn't entrust my passwords to them. Most password managers store the data on their companies' servers, and if those servers get hacked, your passwords will quickly fall into the wrong hands.
Effective wireless security tips for entrepreneurs
Wireless networks can often be a nightmare, especially for business owners. They make company devices vulnerable to new attack vectors, which aren't effective over a wired network. Still, there are several tips that you can apply to increase the security of your Wi-Fi. Here are the most effective ones.
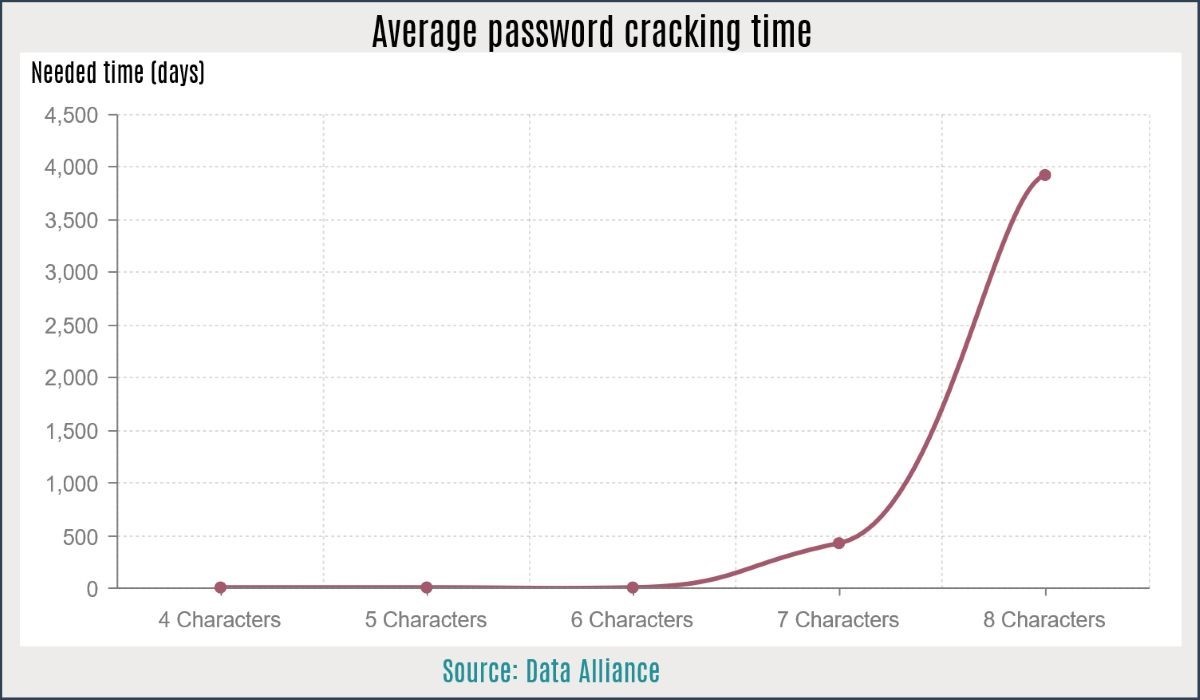
Use strong passwords. These days, it is easy to rent a computer farm, and then run large-scale brute force attacks until the password is cracked. Here's a graph from Data Alliance which shows how how long it takes to crack a complex password of up to 8 characters, depending on its length. So, if any of your passwords has less than eight characters, it’s time to change it right now.
Utilize the strongest wireless encryption mechanism that is available. Today, we are talking about WPA2, but the improved WPA3 will be released soon. Things may change by the time you're reading this article, so ensure that you keep an eye on the Wi-Fi Alliance website. The first device that should be upgraded is your router; it’s your first line of defense, so make sure to replace it as soon as new technologies become available.

How to stay safe online while you are traveling
Most business owners need to travel from time to time. And many of them need to connect to the Internet while they are traveling, because they need to access company data, have VoIP-based conference calls, and so on.
Still, while people are on the go, the risk of getting their devices infected grows exponentially. For starters, they aren’t protected from intruders by the solid hardware and software solutions that they’ve implemented for the company network. So, what can we do to minimize the risk of getting a company laptop infected with spyware or any other sorts of malware? Read on to discover several key tips.
Begin by ensuring that your portable devices, be them laptops, tablets or cell phones, have antivirus protection, and that the virus database definitions are up to date. While many people know that PCs and Macs are vulnerable to malware, most of them treat mobile devices differently. It is true that the number of malware apps that have been built for mobile devices is less than 10% in comparison with their desktop-based counterparts, but the percentage is constantly growing, and mobile devices are used for business-related purposes in larger and larger numbers.
TOP 5 SOURCES OF SPYWARE INFECTIONS
File sharing services;
Freeware/adware applications;
Unsolicited email attachments;
Infected USB drives;
Compromised website pages.